IDS vs IPS: What is the Difference?
We describe the characteristics, advantages, and disadvantages of intrusion detection systems (IDS) versus prevention systems (IPS).

Intrusion detection and prevention are two general terms that describe the application security practices used to mitigate attacks and block new threats.
The first is a reactive measure that identifies intrusion detection. Capable of detecting existing malware such as Trojans, backdoors, rootkits) and detecting social engineering attacks such as man in the middle, phishing that manipulate users for the theft of credentials and confidential information.
The second is a proactive security measure that uses an intrusion prevention system to block preventive application attacks. This includes inclusions in remote files that facilitate malware injections and SQL injections, used to access a company’s databases.
What is an Intrusion Detection System (IDS)?
An IDS is a hardware device or software application that uses known intrusion signatures to detect and analyze incoming and outgoing network traffic for abnormal activity.
This is done through:
- Comparisons of system files against malware signatures.
- Scanning processes that detect signs of malicious patterns.
- Monitoring user behavior to detect malicious intent.
- Monitoring system configurations and settings.
- Monitoring incoming and outgoing network traffic from devices
When detecting a security policy violation, a virus, or a configuration error, an IDS can expel an infringing user from the network and send an alert to security personnel.
Despite its benefits, including in-depth analysis of network traffic and attack detection, an IDS has inherent drawbacks. Because it uses previously known intrusion signatures to locate attacks, newly discovered 0 Day threats may remain undetected.
In addition, an IDS only detects ongoing attacks, not incoming attacks. To block them, an intrusion prevention system is required.
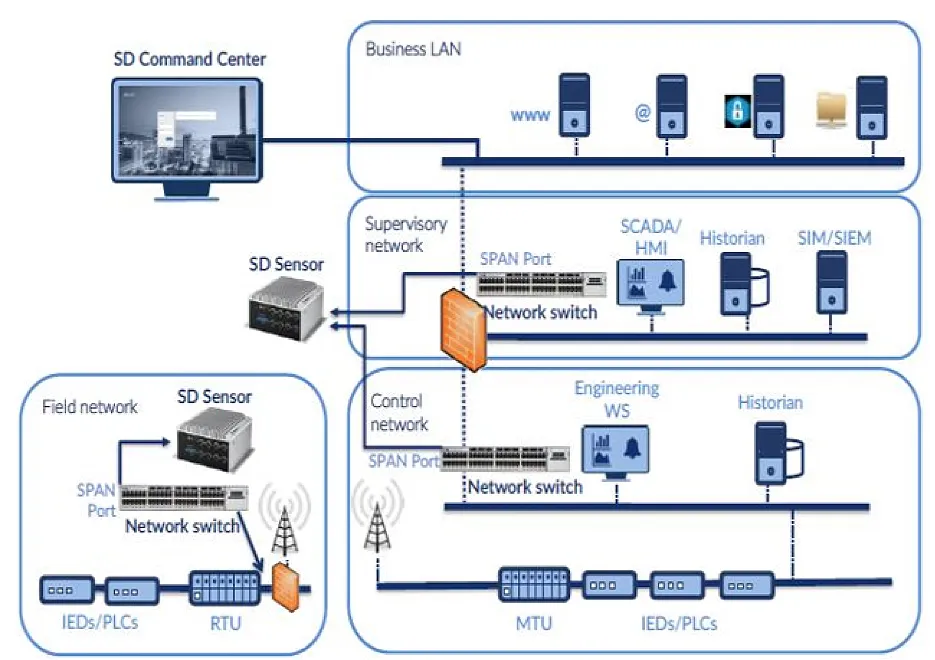
What is an Intrusion Prevention System (IPS)?
An IPS complements an IDS configuration by proactively inspecting a system’s incoming traffic to eliminate malicious requests. A typical IPS configuration uses web application firewalls and traffic filtering solutions to protect applications.
An IPS prevents attacks by discarding malicious packets, blocking offensive IPs, and alerting security personnel to potential threats. This system generally uses a pre-existing database for signature recognition and can be programmed to recognize attacks based on traffic and behavioral anomalies.
While effective at blocking known attack vectors, some IPS systems have limitations. These are commonly caused by an over-reliance on predefined rules, making them susceptible to false positives.

Logitek Optimizes the Security of your OT Network
At Logitek we implement IDS/IPS solutions for industrial environments and Edge versus mission-critical environments. designed for use in Tier 1-3 environments versus mission-critical assets or at the Edge. Its transparency and ability to detect your OT network traffic and production assets are intended to fit seamlessly into your network without disrupting operations.
If you need more information about IDS or IPS systems, do not hesitate to contact us.





